cPHulk is a Brute Force Protection component provided by cPanel software. It detects multiple invalid login requests made to the server’s services and applies the blocks according to the cPHulk component settings. cPanel provides a web-based interface to manage cPHulk settings along with the ability to manage them via the Secure Shell.
By default, HostPapa loads a fully optimized configuration of the cPHulk Brute Force Protection service settings to the provisioned servers. The configuration can still be tuned/adjusted by you or the support team (by your request).
cPHulk Brute Force Protection is a complicated component, and its functionality cannot be covered in a single article. You can check out the official documentation to learn more.
In this article, you will learn:
- How to access the cPHulk component
- What types of access the cPHulk component is locking down
- Configuration settings
- Whitelist management
- Blacklist management
- Countries management
- History reports
How to access cPHulk component
The cPHulk Brute Force Protection component is available for the root users only (System Administrator user). You can access it from the root WHM control panel.
| Home » Security Center » cPHulk Brute Force Protection |
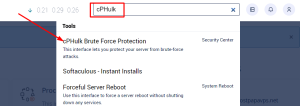
You can also use the WHM search box to find cPHulk Brute Force Protection.
What types of access the cPHulk component is locking down
If cPHulk detects too many failed login attempts coming from a single IP address, then it locks down access from that IP address to the following services:
- cPanel services
- WHM services
- Mail services (Dovecot® and Exim)
- The FTP service
- Secure Shell (SSH) access
Since the cPHulk is working with the authentication modules in cPanel, it doesn’t lock access to the website itself or the delivery of emails. It is affecting users who are attempting to log in to the services listed above only. If the IP address was blocked by cPHulk due to the number of the failed login attempts, then all further authentication attempts from that IP address will be rejected until the block expires or manually removed from the IP address of the user.
This security system protects you by blocking malicious users from accessing your server/accounts by guessing your passwords (brute force attacks).
Configuration settings
While HostPapa is uploading a fully optimized configuration of the cPHulk Brute Force Protection to your server, you may still need to adjust the configuration of the cPHulk Brute Force Protection component set up according to your needs. This can be done from the Home »Security Center »cPHulk Brute Force Protection under the [Configuration Settings] tab.
Within this area, you can adjust the security settings for the following areas:
- Username-based protection
- IP Address-based protection
- One-day blocks
- Login history
You can also adjust the setting of the notification preferences at the bottom of the page. Please be sure to click the [Save] button before leaving the page.
Whitelist management
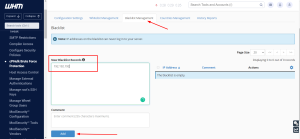
This can be accessed from the Home »Security Center »cPHulk Brute Force Protection under the [Whitelist Management] tab.
Within this area, you can perform a whitelisting of the specific IP addresses for which the cPHulk Brute Force Protection service will exclude its rules. The feature allows adding the comment to each whitelisted IP address and removing the IP address from the whitelist.
It is recommended that you whitelist your WAN IP address in the cPHulk Brute Force Protection settings once you’ve reached the server the first time. That should help you to avoid blocks of your IP address while you are working on your projects.
Blacklist management
This can be accessed from the Home »Security Center »cPHulk Brute Force Protection under the [Blacklist Management] tab.
Within this section, you can find the list of the IP addresses already blocked by the cPHulk Brute Force Protection and apply a manual block for the IP addresses. The feature supports bulk blacklisting, and you can list the IP addresses (one IP address per line) that you want to block, leave the comment that contains the reason for the block, and click the [Add] button to save changes.
Countries management
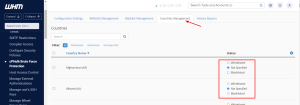
This can be accessed from the Home »Security Center »cPHulk Brute Force Protection under the [Countries Management] tab.
Within this selection, you can either whitelist or blacklist the entire country. You can find it helpful if you are working in your local country area only. In this case, the logins from other countries could be blacklisted by default to improve your server’s security.
History reports
This can be accessed from the Home »Security Center »cPHulk Brute Force Protection under [History Reports].
This area allows you to check existing security blocks, investigate suspicious activity, as well as remove blocks, and clear the reports.
Please keep in mind that when you disable cPHulk, existing account locks will remain. It’s recommended that you removed existing security blocks before deactivating the cPHulk Brute Force Protection component on your server.
If you need help with your HostPapa account, please open a support ticket from your dashboard.
